Cybercrime is ever prevalent and is expected to cost the world 13.82 trillion US dollars by 2028. All businesses must up their game in terms of cybersecurity measures to avoid the financial and reputational damage caused by cyberattacks and to protect customers from being scammed.
Protecting the private and sensitive information of your customers and prospects will undoubtedly be a top priority for your IT function. Customers will rightly expect the best data security and internal safety protocols to be in place when they use your online platform or portal.
One way to achieve maximum online security is through digital authentication methods. These were first invented in the 1960s with the password. Authentication methods have since evolved, with one-time passwords emerging in the 1980s, CAPTCHAs in the 1990s, multi-factor authentication in the 2000s – and today – passwordless authentication.
Read on to explore the concept of passwordless authentication, its various types, and its pros and cons.
How does passwordless authentication work?
Passwordless authentication verifies users without using passwords. It's a user login mechanism that doesn't require a user-generated password, PIN code, answer to a security question or any other authentication token that relies on an individual's personal knowledge. Passwordless authentication is a much safer option compared to single-factor authentication, which often requires a password used in combination with a unique user ID (for example, a username, email address or phone number).
So, how exactly does passwordless authentication restrict unauthorised users? Via the alternative, unconventional login methods that we'll come onto shortly in this article.
The benefits of passwordless authentication
First though, let's look at three key advantages this cutting-edge cybersecurity measure can bring to your business.
1. Better security
Passwordless authentication protects customers from falling victim to certain cyberattacks that rely on bypassing passwords, such as brute force and phishing attacks. It also helps prevent credential theft, as no passwords can be stolen or exploited.
Uku Tomikas, Messente's CEO, further explains: "If your business uses passwordless authentication and you experience a data breach, the damage that can be done is limited. This is because the factors used for passwordless authentication can't be stored in advance, so effectively, there are no credentials to steal! That said, it's not 100% risk-free – no online security method is. Even with passwordless authentication, sensitive customer data can still be compromised."
2. Improved UX
From the customer's perspective, passwordless authentication is much more user-friendly than password-based authentication. There's no need to remember complex 'strong' passwords, and logging into an application is smooth and quick because passwordless authentication methods typically involve 'one tap' or virtually instant biometrics scanning.
Passwordless authentication helps keep customer accounts secure no matter the device they use. And it's flexible – you can use different methods across different communication channels.
3. Cost-efficiency
Passwordless authentication reduces the need for 24/7 technical support. Because customers will no longer forget their credentials or get locked out of their accounts by repeatedly entering incorrect passwords. They won't be subject to phishing attempts either.
Additionally, as a passwordless authentication process reduces the chances of security incidents, like data breaches, you can save on the potential costs associated with such events. For example, mitigation, data recovery and brand reputation repair.
Two common passwordless authentication methods
Passwordless authentication is performed using either possession or inherence factors. We explain what these are, plus their associated pros and cons, below:
1. Possession factors
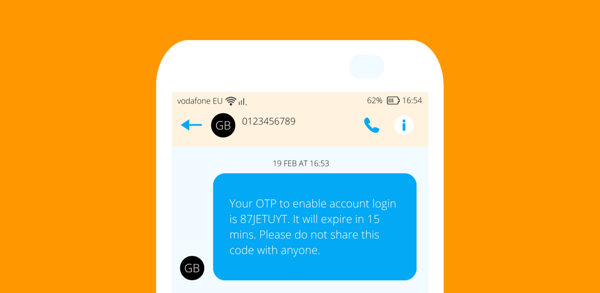
Rather than being based on information customers know, possession factors are something that customers or users have in their physical or digital possession. This could be a device, one-time passcode (OTP), or web link.
An example is an OTP delivered to a phone number for SMS verification. OTPs can also be sent via email and other channels. Wise, the international money transfer application, sends OTPs via WhatsApp if SMS messages or mobile push notifications aren't being delivered for any reason.
Hardware tokens, such as smart cards, USBs and key fobs, are also considered possession factors – as are 'magic links' – one-time login links sent via SMS or email. Then, there are authenticator apps, e.g., Google Authenticator, which provide a time-limited PIN code that refreshes every minute.
Possession factors – pros and cons
Pro – possession factors are harder to bypass or crack compared to knowledge factors because a hacker would have to gain remote access to the customer's device or hardware token. That's not impossible, but it's much trickier than running a straightforward brute-force password attack.
Pro – OTPs and magic links are more convenient for users because they don't have to remember any credentials. Instead, they simply copy and paste a temporary PIN or tap on a link to log into an application.
Con – this type of authentication factor can be lost or stolen and end up in the wrong hands. However, hackers can't do too much damage with a possession factor if it's being used in combination with a knowledge factor, e.g., an answer to a security question.
Con – hardware tokens can be costly when you consider that every customer will need one (there's also the distribution and management of them to think about too).
2. Inherence factors
Inherence factors rely on intrinsic traits unique to individual users. These include biometric technologies such as facial recognition, fingerprint or retina scanning and voice recognition, as well as behavioural characteristics like voice patterns and keystrokes – even the way a user holds their mobile device.
Some biometrics use liveness detection techniques to identify whether the source of a biometric sample is a live human. iPhones do this as a way to overcome security vulnerabilities – they use AI to ensure the mobile user is awake when scanning their face to unlock their phone.
Pros and cons
Pro – inherence factors are believed to be the strongest of all authentication factors, as users must present verification evidence that's unique to who they are.
Pro – users experience the lowest levels of friction with inherence factors. For example, it's even quicker and easier to scan a fingerprint than it is to enter an OTP.
Con – some inherence factors, like facial recognition, can be manipulated, e.g., by using a high-quality photo or video of the authorised user. However, this risk is reduced by using liveness detection.
Con – not all users will have reliable biometric sensors available on their devices.
How to implement passwordless authentication with Messente
Messente is a global business text messaging service commonly used for customer verification. You can send OTPs and magic links by SMS to more than 190 countries and set up fallback options via Viber in the event some texts can't be delivered due to a technical problem at the customers' end.
Getting started with Messente is simple:
1. Sign up for a free Messente account.
2. Receive your API key (secure ID).
3. Verify your business as a sender.
4. That's it – you're ready to start sending automated OTPs or magic links by text!
Related: Discover how tech company Onde saw a 30% cost reduction after sending OTPs with Messente.
Enhance online security with passwordless authentication
Passwordless authentication makes it more difficult (and costly) for cyber criminals to gain access to customer accounts. It reduces vulnerabilities and helps keep customers protected from phishing attacks and credential theft. If you experience a data breach, the damage will be limited in that there aren't any user login credentials to steal. Importantly, passwordless authentication improves the user experience, making it quick, easy and frictionless to log into an online application.
Finally, although a passwordless system can be expensive to set up, your business could also save money by reducing the number of helpdesk enquiries relating to account login and password resets.
Want to learn more about how passwordless authentication works with Messente? Book a discovery call today.